Types Of Cyber Security Attacks Pdf

Access legit or otherwise to device storing data powers granted determine the state of data driven services.
Types of cyber security attacks pdf. Gaining or attempting to gain unauthorized access to a computer system or its data. Cyber space iot and network security. In mobile ad hoc network the nodes are independent. Installation of viruses or malware that is malicious.
Cyber security protects the integrity of a computer s internet connected systems hardware software and data from cyber attacks. A drive by download can take advantage of an app operating system or web browser that contains security. Now a day most of the people use computer and internet. This paper surveys aim to discuss the most common cyber security attacks types what the mechanisms that used in these attacks and how to prevent the system from.
Looking back it is easy to identify the different generations of attacks and security products that protect against them. It uses malicious code to alter computer code logic or data and lead to cybercrimes such as information and identity theft. Network security is main issue of computing because many types of attacks are increasing day by day. Here s an overview of some of the most common types of attacks seen today.
Types of cyber attacks bad data injection goal. A cyber attack is an exploitation of computer systems and networks. We are living in a digital era. Types of cyber attacks.
Like a word document or pdf attachment but actually has a malware installer hidden within. Types of cybersecurity attacks. Without a security plan in place hackers can access your computer system and misuse your personal information your customer s information your business intel and much more. Real world consequences potentially catastrophic.
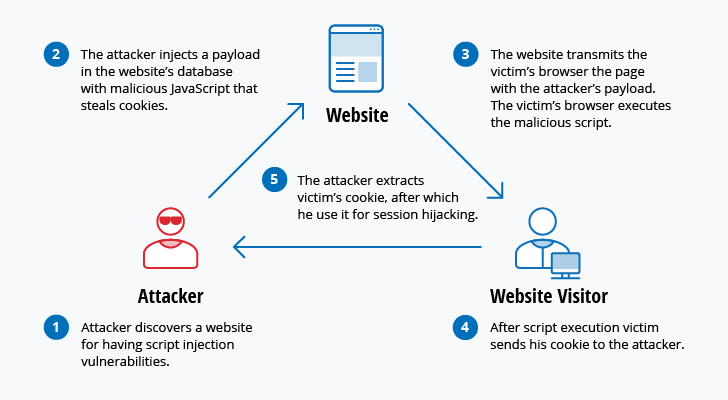
Download full text pdf read. Unwanted disruption or denial of service attacks including the take down of entire web sites. What are the most common cyber security attacks being performed today. Denial of service ddos aims at shutting down a network or service causing it to be inaccessible to its intended users.
Let us tell you about them. The attacks accomplish this mission by overwhelming the target with traffic or flooding it with information that triggers a crash. 5th generation cyber attacks are here and most businesses are behind background in the last 25 years attacks and security protection have advanced rapidly. To submit incorrect data to a system without detection.
Unlike many other types of cyber security attacks a drive by doesn t rely on a user to do anything to actively enable the attack you don t have to click a download button or open a malicious email attachment to become infected.